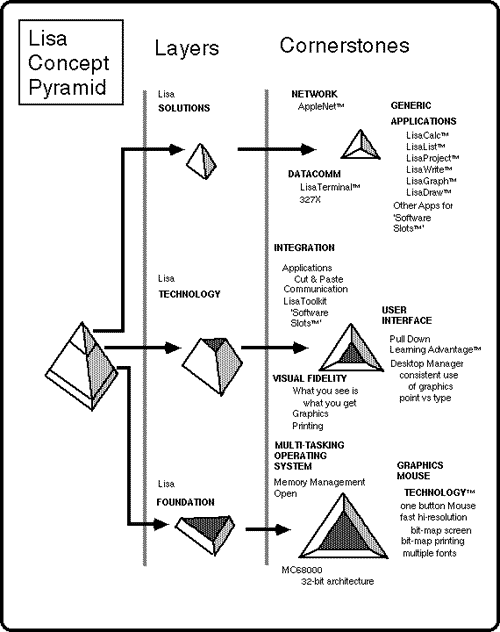
LISA TECHNOLOGY The Lisa computer has proven to be one of the computer industry's most underrated personal computer systems of the last decade. When Apple released the Lisa in 1983 very few people seemed to understand the revolutionary concepts introduced by the Lisa. This misunderstanding, in retrospect, was also present at Apple. Apple's philosophy behind the Lisa can be summed up in two words: Lisa Technology. This technology is a combination of hardware and software technology. What made the Lisa a revolutionary computer was the integration of its hardware and software and the desire by its designers to make the computer as easy to use as possible without sacrificing the user's ability to accomplish significant computing tasks. In Apple's words, Lisa Technology was based upon "the extensive use of graphics, consistent user interface, and pointing device (the 'mouse') which together emulate the way an individual works in the office". Lisa is a system that has to be used extensively before it can be appreciated. In the words of one of Apple's Lisa documents the Lisa hardware and software combination "must be seen to be believed". Telling people about Lisa's important differences will only cause your credibility to drop because they will not believe you. Lisa is really different. Demonstrating the system is some help, but not a lot. There is always the nagging question, "Can something that looks so gimmicky really do any serious work?" While there are people who have tried Lisa and really don't like it, I think that most people who spend several hours with a Lisa doing real work will come away with positive conclusions about the Lisa's value (or at least the value of its technology). One effective presentation tool used by Apple for Lisa customers was the Lisa Concept Pyramid. The next figure is a diagram showing this pyramid. The top part of the pyramid represents the solutions required by the target customer, the information professional (also called "knowledge workers" by Apple). The generic applications are all tools which can be used by almost anyone. The middle layer of the pyramid represents the technology that had to be created in order to produce a truly "easy to use" system. The original prototype of this kind of technology was created within Xerox PARC. This is where the bulk of Lisa's 200 man-year effort went in developing Lisa. Many of the refinements and contributions of Apple are in the areas of Integration and a User Interface that is easy to learn and use. The one button mouse and the software to allow that was key to that accomplishment. The third cornerstone is Visual Fidelity, or what you see on the screen is exactly what you get when printed. The bottom layer is the foundation for the layers above. The major design issues were all dictated by the needs of the software rather than the traditional way in which the hardware dominated the design. The Lisa operating system needed to be multi-tasking to allow multiple programs to co-exist at once on the screen. The Graphics Mouse Technology is the key to making the Lisa's user interface possible. Note: Apple Computer created this figure as a LisaDraw example. |

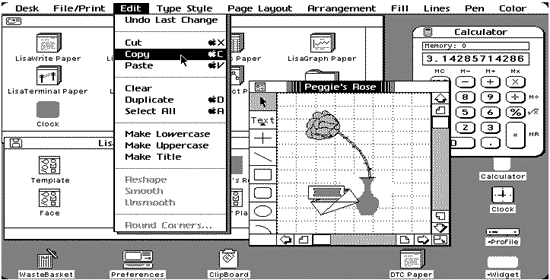
A graphical overview of a typical Lisa screen should help the reader better understand the Lisa's features that made it unique in 1983. For those readers with a knowledge of the Macintosh or other object-oriented systems (eg Microsoft Windows for the IBM PC), the following will be rather boring. The next figure contains a screen image of the Lisa showing several key components of the Lisa's user interface, one of its major distinctive features. The Lisa screen contained a menubar at the top that allowed the user to select commands using the mouse. The screen shows the Edit menu selected with the mouse pointer preparing to activate the Copy command. Arranged on the Desktop are several windows and icons. Windows display file data or file directory information to the user. Several windows are visible with some overlapping others. The front-most window is a LisaDraw window showing a freehand drawing of a rose. The menubar is owned by the font-most window so in this case shows the various major command groups available for LisaDraw. All Lisa user actions were centered around the one-button mouse. The user moved the mouse pointer (usually a small arrow-shaped pointer) to the screen object of interest. For example, to activate a menubar command the user moved the mouse pointer to the appropriate command group label, eg Edit, and pressed the mouse button. The selected menu would then "pull down" showing a list of the specific commands the user could work with. Still holding the mouse button down the user dragged the mouse pointer to the desired command, eg Copy, and released the mouse button when the mouse arrow touched the Copy command and the command name in the menu was hilighted. At this point the selected menu command was activated and performed its function on the selected window object. For example, if you were using LisaWrite, the Lisa's word processor, you could copy data from a LisaWrite document by first selecting with the mouse pointer the text to copy, and then activating the Edit menu Copy command. |
The Lisa's technology for the most part has been copied by other systems both in Apple and elsewhere. But in my opinion several aspects of the Lisa's design made the Lisa unique. These aspects to date have not been adopted by other microcomputer systems to any significant degree.
SOFT POWER-ON AND POWER-OFF The Lisa was powered on by a button on the front plate of the computer case. This same button also powered off the Lisa. The difference tho here was that the Lisa's power button was not a true power button. The Lisa was never turned off, it was always running. When the Lisa was "off" it was really in a low-power mode that only waited for the user to press the power button. If powered-on and the user pressed the power button to turn the Lisa "off" the Lisa told the operating system of this fact. The operating system (really the Lisa Desktop Manager) then commanded all executing programs to save their document's data. When all programs indicated that they had saved their documents the Lisa then powered-off to its low power mode.
SELF-ORGANIZING DESKTOP In conjunction with the Lisa's soft power-on/off button the Lisa maintained an orderly desktop for the user. When the user power-off the computer the Lisa's Desktop Manager would save all open document data to disk AND save the state of the desktop too. When the user powered-on the Lisa the Desktop Manager restored the desktop state as it was when the user powered-off.
DOCUMENT-CENTERED VIEW The Lisa supported a document-centered view. In this view documents were important, not programs. To start a new document the Lisa user tore off a sheet of "stationary" from a stationary pad icon that resided on the screen. Each Lisa program came with a stationary pad. When "opened" by the user a stationary pad automatically duplicated itself, set its name to the current date, and created a window on the screen for the user. The Macintosh in System 7 supports stationary pads, but the Macintosh does not use a document-based view. Program icons were really not important on the Lisa except to move the program file to another disk. Generally, Lisa user's kept their document stationary pads in an easily accessible location on the screen and kept the program icons in a folder which they generally never opened except to add new programs or delete old programs.
RELIABLE FILE DATA STORAGE The Lisa's file system was designed to be reliable. To reduce the impact of a system crash, the file system maintains distributed redundant information about the files on the disk storage. Duplicate copies of critical information were stored in different forms and in different places on the disk media. For example, the information in the central disk catalog about a file was also stored in a special disk block at the head of that file. Also each block on the disk specified the part of the file to which it belonged (this information was called a block "tag"). Since all the files and blocks on a disk were able to identify and describe themselves, there were several ways to recover lost information. A utility called the Scavenger was able to reconstruct damaged disk catalogs from the redundant information stored about each file. In my experiences with the Lisa I've only had one Lisa disk that the Lisa scavenger could not fix. The scavenger is activated by the Lisa whenever the Lisa determines that a disk has problems. At this point the Lisa's low-level operating system informs the Desktop Manager which displays a dialog for the user. The user may then select to either have the Lisa repair the disk or eject it. The Lisa's ProFile hard disk and Twiggy floppy drives also supported an extensive set of reliability features. Once such feature was disk block sparing. When a disk block (a unit of 512 bytes on the disk) was detected by the Lisa as beginning to fail, the Lisa's disk drive (either the ProFile or Twiggy) moved the data to a spare area of the disk media. The failing disk block was marked as "bad". Whenever a program attempted to access a bad block the disk drive automatically used a "spared" data block instead. The original Macintosh used to support block tags at the hardware level, but Apple never provided a Scavenger program at the software level to use these tags. Neither did Apple's Finder program (the Desktop Manager equivalent) support any checks for failing disk blocks. After several years Apple abandoned disk block tag use, tho Apple has now introduced the use of block sparing for high density floppies and hard drives.
UNIQUE SYSTEM SERIAL NUMBERS Each Lisa contained a unique serial number which the Lisa Desktop Manager could read (the serial number was stored in a special electronic chip). The Lisa used the serial number for program protection and for establishing unique communication nodes for the Lisa data network.
SIMPLE BUT EFFECTIVE PROGRAM ANTI-PIRACY AND DATA PROTECTION All Lisa's provided a simple and effective method of protecting user programs from piracy and data files from snooping eyes of co-workers.
When the user installed a new program the Lisa "serialized" the disk copy of the program. This serialization process wrote the Lisa's serial number to the program floppy disk. The user of this floppy disk would then be unable to copy this "protected master" program file to another Lisa. But the user could execute the protected program from the floppy disk, a rather tedious task given that the Lisa programs tended to be rather large and floppy disk based program execution would try the patience of most users. Document protection was provided by a password scheme. The user could select a document icon with the mouse and thru a menu command obtain general information about the document via a dialog. This information included the document's size and the protection password. If the user typed a password into this informational dialog the document was protected. When a user attempted to open a protected document the Lisa displayed a dialog asking for the password.
NON-PHYSICAL FILE NAMES The Lisa Desktop Manager did not display physical document names to the user. Instead the Lisa presented the user with a document name "view" which made the user think that the Lisa stored document names with up the 63 characters. The underlying Lisa file system allowed file names to be up to 31 characters in length and the file names could not contain the directory separator characters, "-". The Lisa Desktop Manager maintained for each document a user document name (eg "Vacation Plans - 1983") and a physical low-level file name (eg "{T3D456}"). This non-physical file name scheme also supported the use of multiple documents with the same name, tho the underlying physical file names were different. In this regard the Lisa mimicked the physical working desktop where a worker could have 5 photocopies of the same document on his desktop at the same time. To the best of my knowledge no other microcomputer currently supports non-physical document names.
PULL-OUT HELP CARD IN THE KEYBOARD The Lisa keyboard contained small pull-out cards. These cards consisted of several firm plastic sheets containing helpful information. The first sheet showed the Lisa keyboard and a layout of all the special keys that the user could type with the Lisa keyboard's Option key. Other cards contained concise information about Lisa operating features such as how to copy documents. Another card was blank and allowed users to write down important information pertaining to the Lisa (eg phone number of the local Apple service center or representative). HARDWARE BASED MEMORY MANAGEMENT The Lisa supported a sophisticated hardware based memory management strategy. This strategy allowed Lisa programs to believe they could access more memory than there really was in the Lisa (note: Lisa contained 1 megabyte of physical memory with about half of it used for the Lisa Desktop Manager and the Desktop Libraries). This strategy also allowed the Lisa to segregate executing programs so that they could not interfer with other programs in the event a program tried to access another program's data when it should not have tried this. In this case the Lisa would stop the errant program and alert the user that the program has been stopped.
ENVIRONMENT WINDOW Lisa provided a simple method for the computer to run radically different operating environments. This method was implemented with the Environments Window. When the Lisa started up it first ran a special low-level program called the environment selector. This program ran a default operating environment if one was present. Otherwise, this program displayed a window for the user allowing the user to select the environment to use. Apple supplied two different environments, the Office System environment (for non-technical end users) and the Workshop environment (for programmers). Other companies supplied additional environments (eg the UNIX environment).
ADJUSTABLE SCREEN CONTRAST AND DIM DURATION CONTROL The Lisa screen contrast could be adjusted by the user with a special program called Preferences. This program also allowed the user to define a duration of inactivity for which the screen would automatically dim and the dim contrast. This feature prevented screen "burn in" which happens when a screen is set to a high contrast and images on the screen burn into the screen's phosphorus.
When automatically dimming the screen the Lisa did not suddenly dim the screen. Instead it gradually dimmed the screen in pleasing dim increments. This was a nice touch on Apple's part which saved the user from suddenly encountering a jarring screen change contrast change from a bright level to a dark level.
PRIVACY FEATURE FOR THE SCREEN For Lisa users who dealt with sensitive data on their Lisa screen and could not allow people to see this data, the Lisa provided a simple screen privacy feature. The user could at any time press some special keyboard keys and the screen would automatically dim (Option-Shift-0 [zero] with 0 on the numeric keypad).
SELF-TEST AND FOREIGN LANGUAGE USAGE VIA THE ATTACHED KEYBOARD The Lisa when powered on ran a special program which tested the Lisa's hardware components. This testing made certain that the Lisa was in well enough shape to run user programs and manipulate user data. Hardware failures caused the Lisa to alert the user with a specific failure error number which could be used by an Apple service center to replace the defective part.
During these diagnostic tests (which took around 3 minutes to execute) the Lisa displayed icons and messages to the user. The messages could appear in either English, French, or German. The Lisa determined which language to use by which keyboard was attached to the Lisa. The Lisa keyboards were self-identifying and provided the Lisa with such information as the keyboard "language". For example, if the keyboard was a German keyboard, then all diagnostic messages appeared in German. Unfortunately, the Lisa's Office System and programs like LisaWrite did not use the appropriate language for its menus and messages based upon the keyboard type.
SPECIAL SERVICE MODE The Lisa contained a special "service mode" which could be activated when the Lisa was powered on. This special feature allowed the knowledgeable user to run some special diagnostic tests on the Lisa. Also supported was a cross-hatch pattern for the screen which assisted the user in adjusting the screen contrast.
EASY SYSTEM DISASSEMBLY Lisas were very easy to disassemble by the user without the use of any tools. Apple allowed the user to essentially disembowel a Lisa except for dangerous portions like the monitor screen. For example, users could remove and replace disk drives with ease by just popping the front off (finger grips are at the base of the front panel) and unscrewing a single screw which held the disk drive in place. |